Prevent Windows shutdown after license expire
Issue
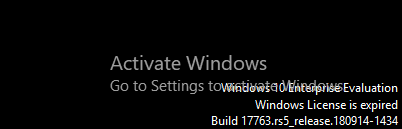
After Windows license expires, you will see a similar message as shown below and then VM will auto shutdown every hour.
Investigation
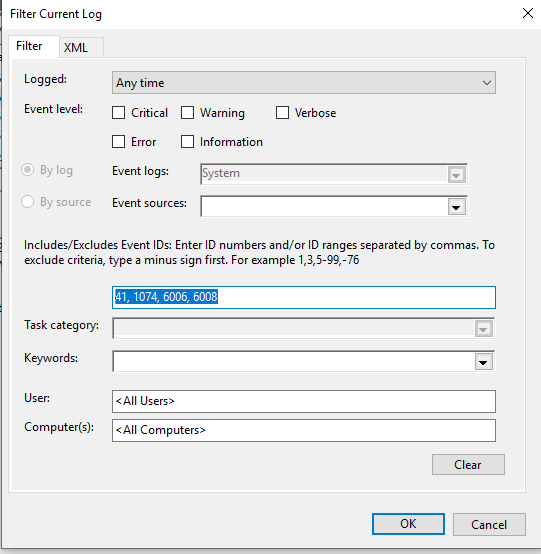
As always, I started my investigation from Event logs. Since we are going to troubleshoot shutdowns, we need to filter messages in logs that are related to restarts. Easiest way to do so is to filter by respective Event Ids. In this case I chose to filter logs by following event ids : 41, 1074, 6006, 6008 as shown below :
A Brief explanation of Event Ids
Event ID 41: The system rebooted without cleanly shutting down first. This error occurs when the system stopped responding, crashed, or lost power unexpectedly.
Event ID 1074: Logged when an app (such as Windows Update) causes the system to restart, or when a user initiates a restart or shutdown.
Event ID 6006: Logged as a clean shutdown. It gives the message, “The Event log service was stopped.
Event ID 6008: Logged as a dirty shutdown. It gives the message, “The previous system shutdown at time on date was unexpected
After applying the filters you will see list of events corresponding to event ids.

Now that we have filtered the events, i decided to look into events that occurred around the time VM rebooted which was around 9:50am

In the General section of the above came across below information :
From the above message it was clear that wlms.exe initiated the reboot.
Next, I opened up task manager and looked for wlms.exe, on further investigation wlms.exe took me straight to WLMS service. WLMS stands for Windows License Monitoring Service and it is installed by default on all Windows Evaluation versions.
How to stop shutdown every hour
Lets take a closer look at WLMS service.
Even though I am logged in with admin account, I do not have access to disable this service . To disable this services please follow below steps :
Download PsExec tools from Microsoft site here
After downloading extract the tool in a folder
open cmd and Run as administrator
cd to the folder path
execute psexec -i -s cmd.exe
This will open another cmd prompt as shown below :

7. Now type whoami to confirm user as shown below:
8. Type services.msc as shown below :

9. This will open services and now you can navigate to Windows License Monitoring Service and can disable it

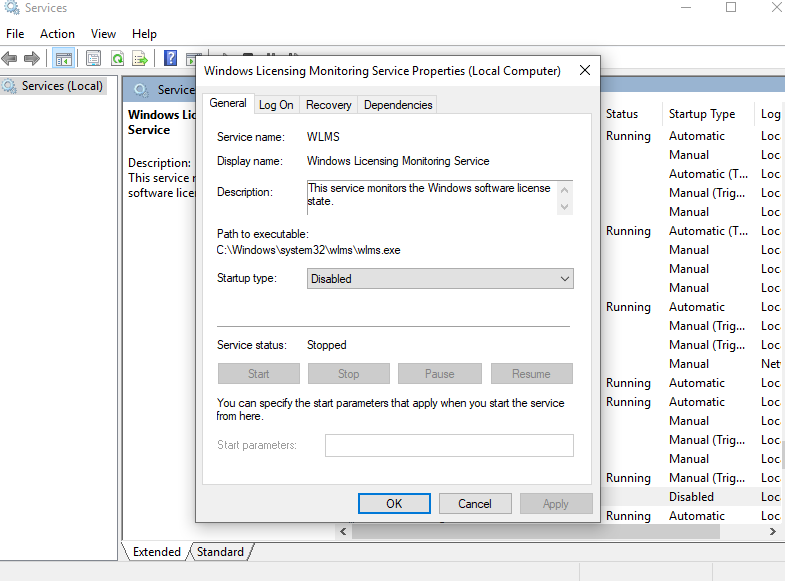
10. Restart the VM
Enjoy! :D
Last updated